- Info@prikustech.com
- Mon - Fri: 10.00 am - 7.00 pm
We are creative, ambitious and ready for challenges!
Over 10 years we help companies reach their financial and branding goals. Prikus is a values-driven technology agency dedicated.
411 University St, Seattle, USA
info@prikus.tech
+1 -800-456-478-23
The Red Team Services offers full-scope testing. The scope covers applications, internal and external networks, facilities, and employees. Red teamers usually attack without the knowledge of the employees. Red teamers work like real-world attackers to simulate a real criminal attack on the organization’s infrastructure. Red Team Services helps your organization to understand existing security controls, implementations, and weaknesses. The objective of a red team test is to obtain a realistic idea of the level of risk and vulnerabilities against your technology, people and physical assets.

The Red Team provides comprehensive security by performing a real-world attack scenario. Red teamers target a compromised organization to gain access to sensitive information in any way possible.
The Red Team cyber security services is a full scope testing leaving no margin for error in testing the organizations resistance to cyber attacks. Prikus Red Teamers execute multi blended attacks on the organization to identify security vulnerabilities emerging from all sides- technology, people and physical assets. On the technology side red teamers test for vulnerabilities emerging from the network, applications routers, switches, appliances and so on. On the human resources side redteamers enter the organization as staff, independent contractors, management, executives, business partners and so on to see if digital assets can be hacked by these people. Red Teamers also try to gain access to physical infrastructures like offices, warehouses, substations, data centers, buildings, and so on.
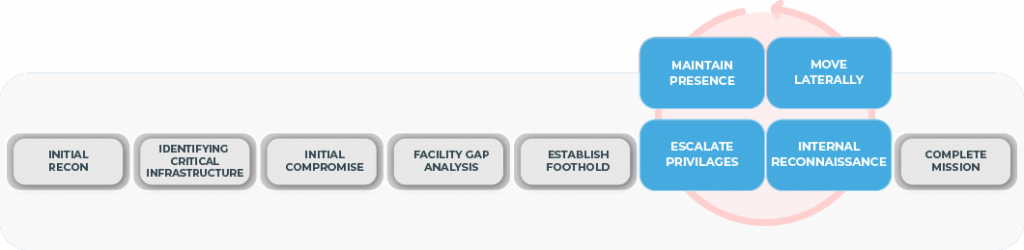
The Red Team relies on a systematic, repeatable, and reproducible methodology. We begin by establishing the following core information and rules of engagement, agreed upon in collaboration with the organization’s leadership team:
In this phase, active and passive reconnaissance is performed to gather information about the organization and its infrastructure
Using the information from the reconnaissance, we identify and target the organization’s critical assets and IT infrastructure.
In this phase, we try to identify further security weaknesses in the identified enterprise’s assets, such as web applications, network, devices, server, etc.
In this phase, we target the organization’s physical security, such as entry gates, door locks, and office boundaries. As a red team, we try to bypass physical security by performing social engineering and other targeted attacks and exploits to bypass the existing security system.
The Red team prepares weaponized exploits for the identified vulnerabilities and gaps in security, exploits the target, and gains access to the assets.
Once the assets are compromised, a backdoor is set up for further exploitation and information gathering.
In this phase, after successfully compromising one service, the Red team performs an internal recon to identify vulnerabilities in the internal servers.
In this phase, to analyze the gathered data and collect further intelligence from the enterprise network, Red team members implement the backdoor.
Once the system backdoors with full access, we prepare a detailed report, including the executive and technical information, and conclude the Red Team assessment.
The identification of vulnerabilities in your system along with the knowledge of major areas of exploitation is critical. But what is more important is to be able to convey to you all this information in a clear and concise way. This report will include all the information about the security controls assessed as well as an analysis of the areas that need to be looked into for achieving the required amount of security.
The report is systematically designed into two parts: The high level management report suitable for the understanding of management personnel, and an in-depth technical document for the technical staff to understand the underlying security risks along with recommendations and preventive countermeasures.