- Info@prikustech.com
- Mon - Fri: 10.00 am - 7.00 pm
We are creative, ambitious and ready for challenges!
Over 10 years we help companies reach their financial and branding goals. Prikus is a values-driven technology agency dedicated.
411 University St, Seattle, USA
info@prikus.tech
+1 -800-456-478-23
How to Detect and Quarantine security vulnerabilities in your AWS Infrastructure within an optimized budget?
Talk with our experts to know more.
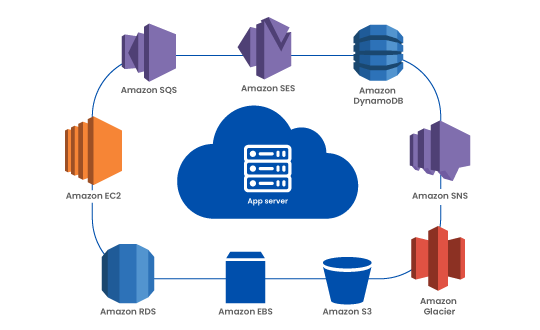
There is a different perspective for penetration testing Amazon Web Services environments to be considered for performing Security Assessment. At Prikus we perform AWS cloud penetration testing considering all the different perspectives for the assessment. To help secure your AWS environments. Prikus AWS penetration testing is a security assessment service that helps improve the security and compliance of applications deployed on AWS.
Our AWS security experts assess the AWS Applications for bad exposures, vulnerabilities and deviations from the best practices. AWS Security Assessment checks for vulnerabilities emerging from unintended network accessibility, misconfigurations, user accounts and their permissions, access management and so on. The security assessment performed will ensure benchmarking of the AWS Application against the predefined rules rules, best practices and vulnerability definitions. The report delivered to enterprises ensures they get a list of vulnerabilities prioritised by the level of security threat and detailed steps to mitigate those vulnerabilities.
Following are the Security Assessment that are performed on an AWS environment
Consider your web application hosted on a VPS or dedicated server and later moved to the cloud platform in which only your developed web application is considered in the scope.
This type of cloud assessment is performed where in the cloud system cannot be accessed externally and is private and which has firewall to prevent direct access and can only be accessed by a bastion host.
Testing the cloud console for any misconfigurations such as the created user accounts and their permissions, implemented ACL, etc. This is more of a configuration review verifying standards policies have been implemented while creating accounts. We can identify different techniques to perform privilege escalation.
Benefits of an Application penetration testing performed by Prikus include: